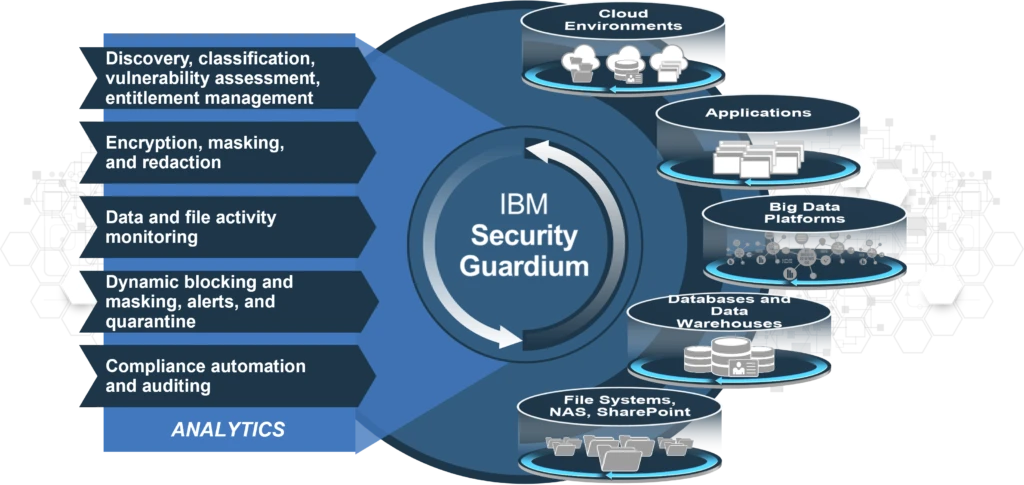
With the superior logging capabilities of the IBM Security Guardium Database Activity Monitoring solution, accesses to databases are recorded instantly without the need for audit logs of database systems. All executed SQL statements are parsed and reported in detail.
With the solution’s advanced policy definition capabilities, alarm rules can be defined for all fields within the SQL sentences executed. For example, an alarm may be generated when a connection is made between application users and application servers outside of the application servers, or when the salary column of the personnel table is queried. The solution allows you to write rules with all the details by parsing the executed SQL statements as well as the connection information. Blocking rules can also be defined for SQL statements considered critical, so the solution can be positioned as a DB firewall.
Sensitive data stored in databases is discovered and classified with the data classification module that comes free of charge in the solution. It can be discovered in which columns of which tables the data considered sensitive by regulations such as GDPR, PCI-DSS and KVKK are stored. The resulting discovery data can be reported and used as input in the report and policy definitions of the solution.
By periodically scanning which types of databases are located on which IPs on the networks, newly added database servers are automatically discovered, thus newly added databases and duplicate databases are detected.
Checking the permissions of users on databases is an indispensable control for both security and audit processes. The authorizations of all users are periodically checked with user role and authorization scanning on the IBM Guardium solution.
With the integrated vulnerability scanning module of the IBM Guardium solution, configurations in databases are evaluated under the headings of configuration, authentication, version and authorization in accordance with the standards set by security authorities around the world. Solution suggestions are offered to eliminate the identified vulnerabilities.
İnkılap Mahallesi Umman Sokak No:4 İç Kapı No:2 Ümraniye / İstanbul 34768