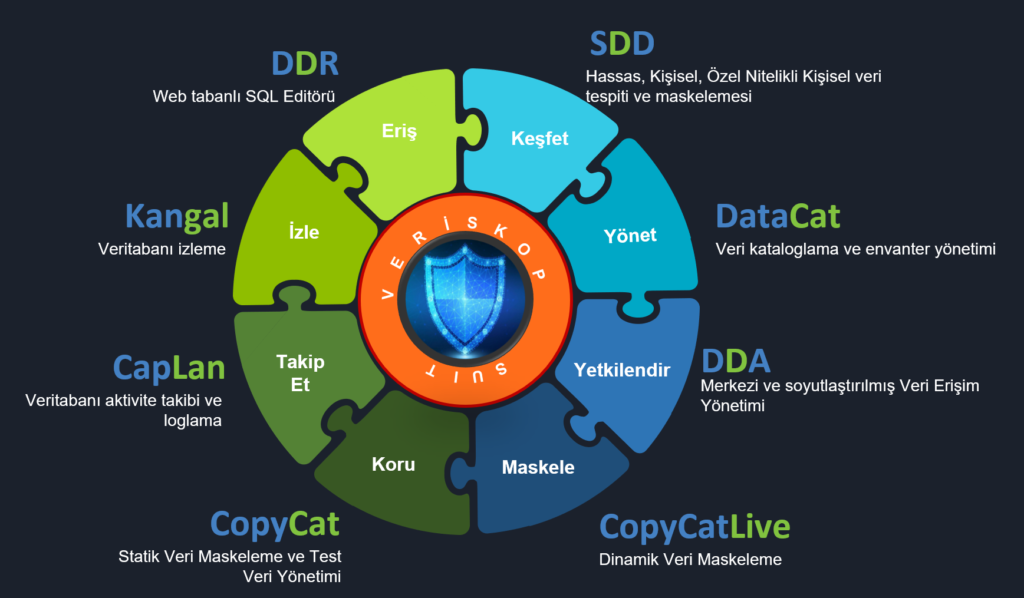
You can discover, classify, label, mask, and manage all your corporate data from a single platform with the Veriskop Data Security Suite solution family. You can combine one or more modules tailored to different organizational needs to create customized solutions for your institution.
With the Veriskop SDD module, you can perform sensitive data discovery on your structured environments (databases) as well as unstructured environments (file servers, email servers, NAS, Office365, SMB, etc.). You can discover areas where your data subject to regulations is stored within the framework of various predefined regulatory compliance policies in the product. Additionally, by defining custom rules for your organization, you can discover data that is sensitive to your specific needs. The Veriskop SDD module facilitates processes such as classification and labeling for the sensitive data you discover. You can integrate the data obtained from here with security solutions like DLP to ensure effective data protection. With this solution, you can mask sensitive data in their respective locations, preventing users with access to files from accessing sensitive information. The solution also supports OCR, allowing all these operations to be performed on image-format files or scanned data.
The Veriskop Datacat module allows you to manage your data like an inventory for your organization. Whether it’s the data you discovered with SDD or the data from your existing data dictionary, it enables you to catalog and manage data like an inventory. It allows you to view and manage the owner of objects, associated applications and units, and what data is stored on them. Additionally, it provides you with data quality statistics.
Our database authentication and authorization tool, DDA, allows you to integrate and centralize the authentication and authorization processes of all your databases with the organization’s Active Directory – LDAP structure. This enables you to standardize user management across all databases and manage authorization approval processes centrally. You can easily perform authorization controls, a crucial component of all audit mechanisms. Additionally, you can identify and automatically revoke unused permissions. You have the flexibility to assign users restricted and time-limited permissions. For example, when a user starts a role as a Business Analyst and is added to the relevant LDAP group, they can automatically have the permissions granted for business analysts across all databases. Or, when you want to provide a user with short-term access to specific tables for a new project, you can progress through the relevant approval chain in the solution and grant the permission, which will be automatically revoked when the specified duration expires.
With our dynamic data masking solution, CopyCat Live, you can easily manage masking operations on data returned from queries to databases through the interface. You can prevent uncontrolled access to sensitive data by applying both row-level and column-level masking. You have the flexibility to manage masking processes on any tables and columns you desire in your databases. You can conceal sensitive data without making any changes to your databases or applications. For example, you can show only the first and last characters of the Turkish Identity Number fields in tables, mask 50% of the Mother’s Maiden Name fields, randomly assign a value between 1900 and 1930 to the year part of birth dates, or choose not to display data for VIP customers in query results.
With the CopyCat tool, managing static data masking operations within the Veriskop solution family, you can statically mask sensitive data in your databases. Especially for test and development processes, required data can be easily generated by masking the data in your databases. The table structure and relationship integrity are maintained in the masking processes, ensuring both smooth operation of your applications and meeting security requirements by not using live data. With the CopyCat solution, you can also easily manage data transfer between different databases. For example, you can transfer data from Oracle to databases such as PostgreSQL, SQL Server, DB2, MongoDB.
Our comprehensive data security product family also includes a database activity monitoring solution. With our CapLan solution, you can monitor all activities on databases, both over the network and locally. You can easily access all historical logs and trace records.
In our data-centric security product family, Veriskop, we also have a solution that allows you to monitor the performance of databases. With our Kangal solution, you can track the health status of databases using performance metrics, and potential performance issues can be detected in advance with notifications sent.
With our web-based SQL editor, DDR, centralized and security-controlled access to enterprise databases can be provided through a user-friendly interface. This helps prevent connections to the database using tools that may have security vulnerabilities due to open-source code or outdated versions.
İnkılap Mahallesi Umman Sokak No:4 İç Kapı No:2 Ümraniye / İstanbul 34768